EMPOWERING GROWTH WITH REAL DATA encryption

MEET invent.co
OUR STORY
We have just started working so that we can create history in encrypting the world.

OUR VISION
Data security and privacy seem to be in the news almost daily. From hacks into various government sites to the latest credit card leaks with major retailers, we are reminded that understanding the risks of data ownership is imperative in today’s digital age. Oral surgery practices must make sure that their data, especially patient data, is secure by implementing a proper security plan.
Since the Health Insurance Portability and Accountability Act of 1996 (HIPAA), requirements to fortify against the improper use and access of patient health information have called for entities to improve protection strategies and tactics. These requirements have only been reinforced with the HITECH Act (Health Information Technology for Economic and Clinical Health) of 2009 and the Omnibus Final Rule of 2013.
When implementing a security plan, you should consider multiple safeguards for data access and data use. It is also important to note, as you develop and implement plans to fortify against potential threats, that “security is not a one-time project, but rather an ongoing, dynamic process that will create new challenges as covered entities’ organizations and technologies change.” (Security 101 for Covered Entities (CMS, November 2004))
Asijit Paul strongly encourages practices to work with both computer and security policy experts to help create and implement a comprehensive security plan. We offer assistance in implementing appropriate network security through invent.co, our office technology and security experts. For more information about invent.co email us invent.co.org.1610@gmail.com or visit us.

OUR TECHNOLOGY
Quantum’s Perspective
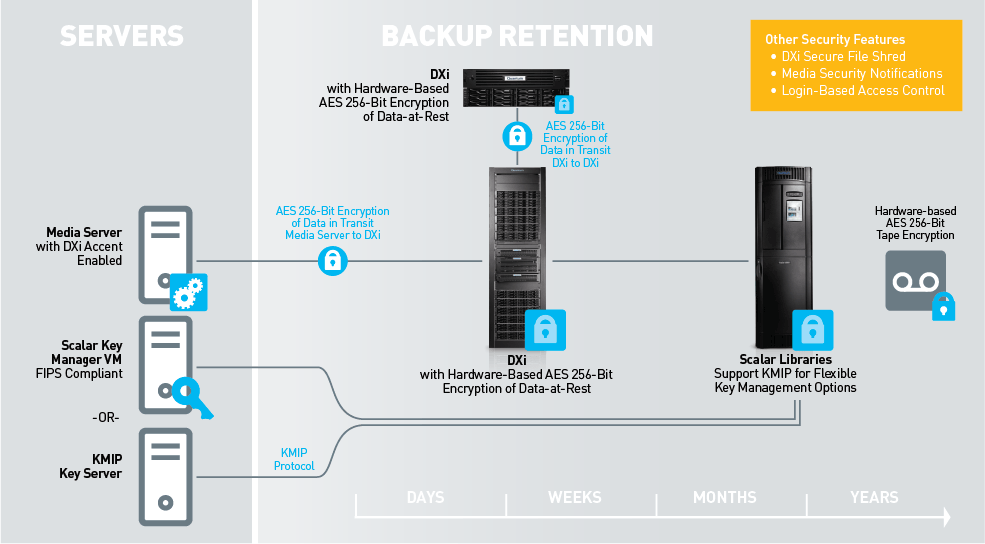
Quantum recommends that IT departments include data encryption as part of their core protection strategy, and can help you integrate the technology easily and cost-effectively into your existing backup, recovery, and archive processes.
End-to-end security solutions help organizations:
-
Meet corporate mandates and even legislative requirements to encrypt sensitive data
-
Protect your company’s reputation
-
Protect against security breaches, whether caused by hard drive removal or by losing tapes
-
Take advantage of encryption without sacrificing performance and your ability to meet increasingly demanding SLAs

USING INVENT.CO







GET IN TOUCH
PHONE- 8961572836
Kolkata, West Bengal, India, 711302

Asijit Paul